Apple has announced the discovery of a critical security flaw in iPhones, iPads, and Macs that may let attackers seize complete control of a victim’s device.

About the Security Flaw
• Who found it?
Apple did not disclose who discovered the vulnerability or where it was found in its reports. Anonymous researchers were credited throughout.
• Did hackers know about it beforehand?
Apple has acknowledged that the flaw was possibly exploited. However, no further information was provided.
• How does it work?
Apple claims that the vulnerability can be taken advantage of by “processing web content,” which means going to a website containing malicious code. By luring an unsuspecting user to such a website, attackers who were aware of the flaw and how to exploit it may take full control of a victim’s device and run any arbitrary code they want.
For security reasons, typically, devices will restrict which parts of the system they will allow code to access. However, this vulnerability permitted code to be executed with access to the kernel. With kernel access comes unlimited access to all components of the operating system, which means the attacker could take complete control of a victim’s device.
Related CVE Number:
CVE-2022-32894
CVE-2022-32893
CVE-2022-32893
The Threat to the General Public
Ritesh Kotak, a cybersecurity analyst, said the recent security flaw discovered in Apple devices demonstrates how any kind of personal information placed on electronic devices is vulnerable and can be ‘weaponized.’
It’s possible that cybercriminals can reverse-engineer the security update and launch attacks on members of the public who haven’t upgraded their devices now that the vulnerability is public knowledge.
Precautionary Measures
Experts in information security have advised users to upgrade affected devices, including the iPhone 6S and later versions, many iPad models, 5th generation iPads and later, all iPad Pro models, the iPad Air 2, and Mac computers running macOS Monterey. The problem affects some iPod models as well. (The latest version of iOS and iPadOS is 15.6.1, while macOS is 12.5.1.)
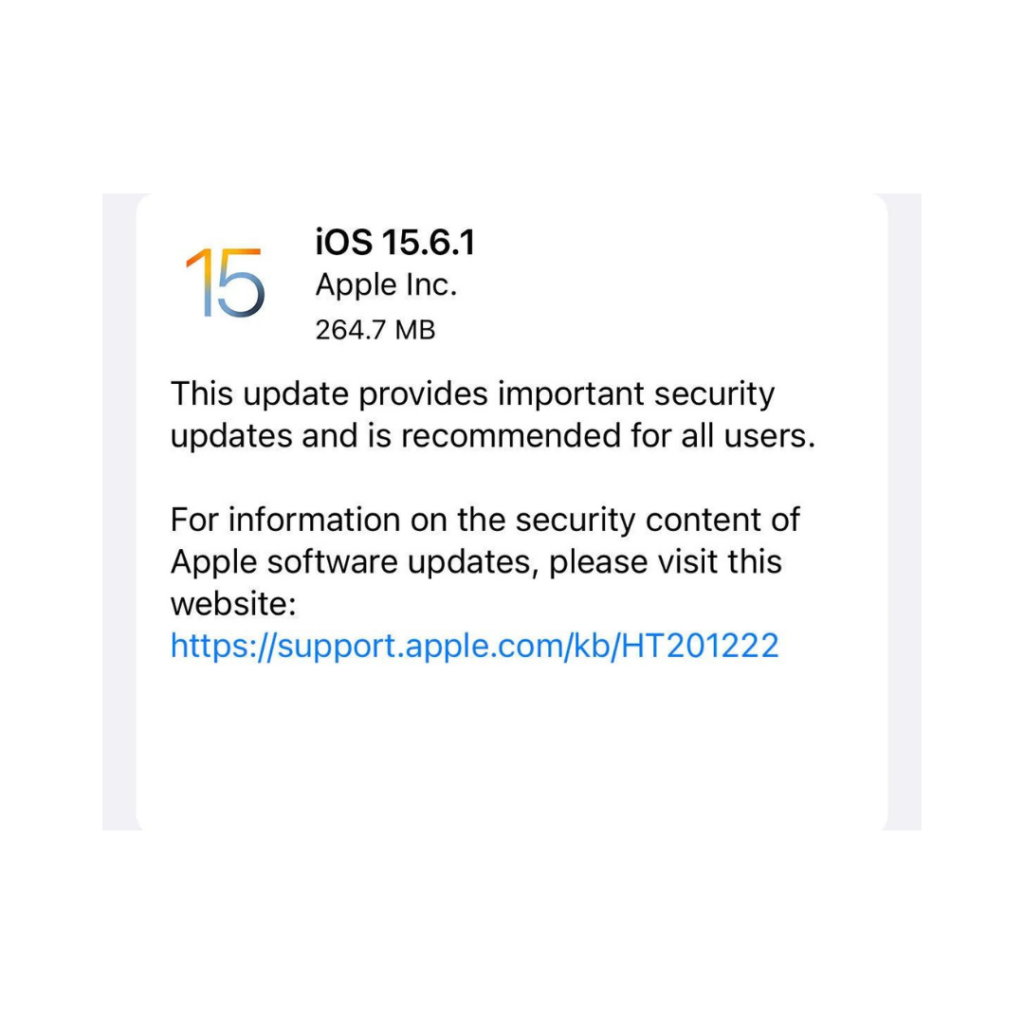
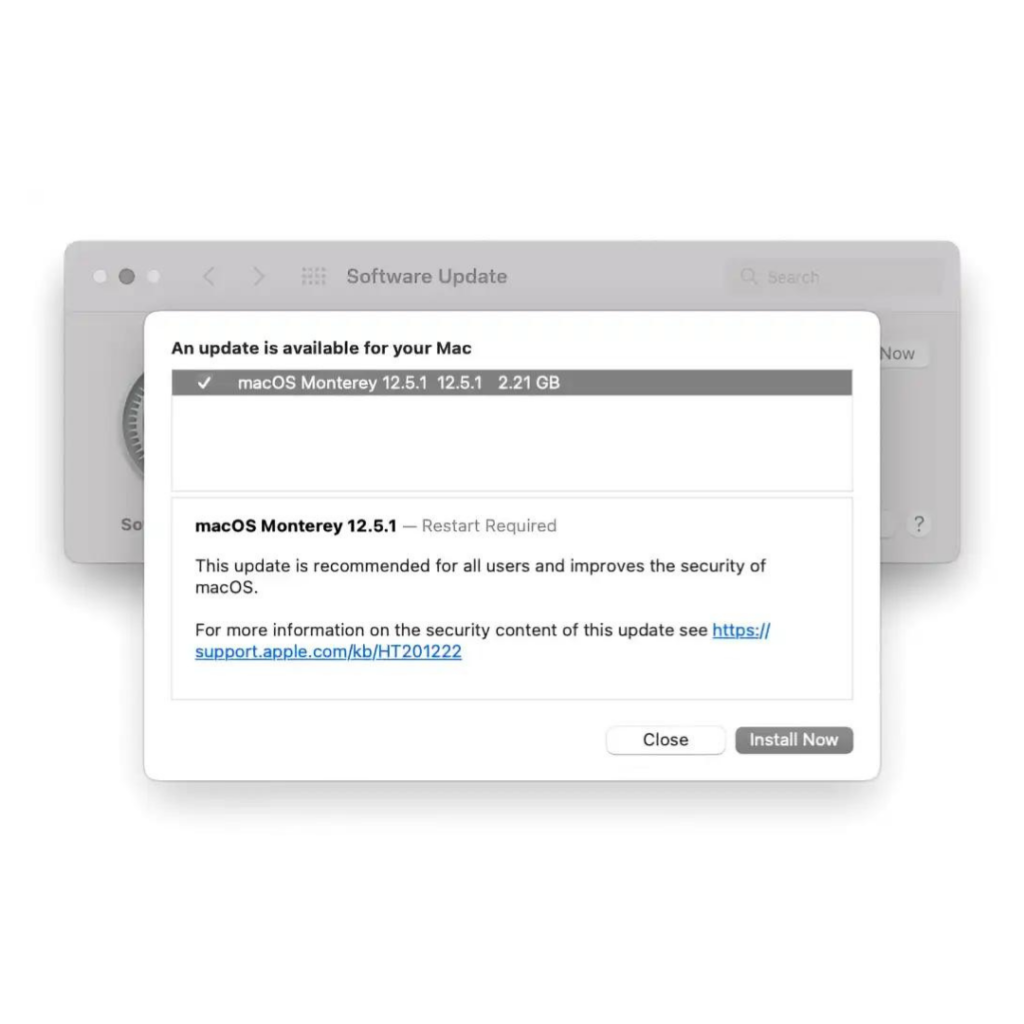
Since the flaw is potentially being actively exploited right now, owners of the aforementioned devices would be prudent to install the most recent software updates on their devices.
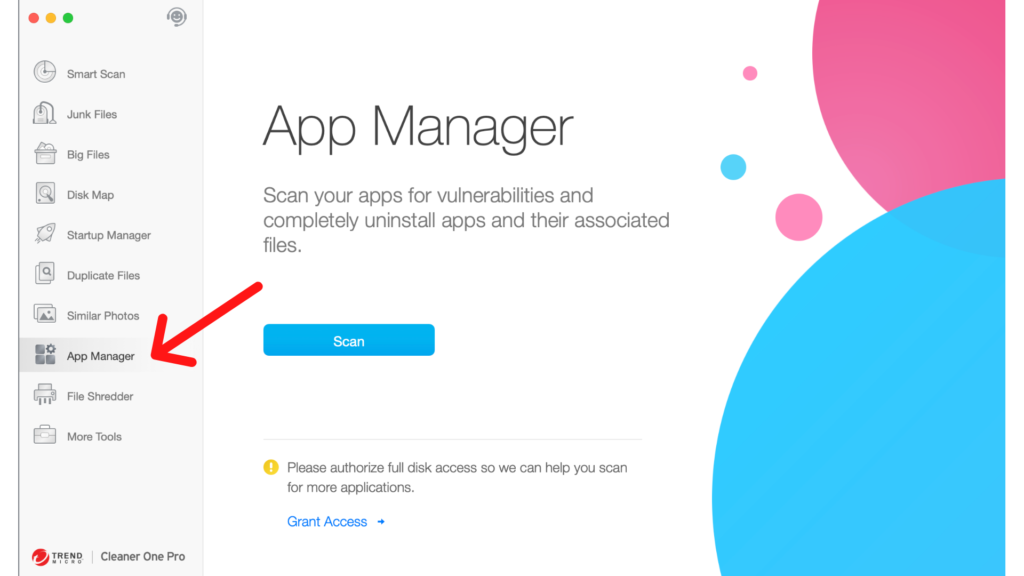
If, after updating your devices, you are still worried about the risks, you can download Cleaner One Pro on your Mac, and use Vulnerability Scan to scan the system for vulnerabilities.
Related Reading:
About the security content of iOS 15.6.1 and iPadOS 15.6.1